
Let’s find out how to set up a secure connection to the server via an encrypted protocol without needing to log in using your account’s password.
Introduction
Using SSH keys is a straightforward and reliable method to secure your server connection. Unlike passwords, it’s nearly impossible to hijack an SSH key. It’s very easy to generate an SSH key.
SSH Key for Linux/MacOS
Open the terminal and execute the following command:
$ ssh-keygen -t rsa
The console will display the following text:
Enter file in which to save the key (/home/user/.ssh/id_rsa):
Press the Enter key. Next, you’ll be prompted to enter a passphrase for additional security of SSH connection:
Enter passphrase (empty for no passphrase):
This step is optional. Simply press the Enter key after this and the next prompt.
Once done, the key will be generated and the console will display the following text:
Your identification has been saved in /home/user/.ssh/id_rsa. Your public key has been saved in /home/user/.ssh/id_rsa.pub. The key fingerprint is: 476:b2:a8:7f:08:b4:c0:af:81:25:7e:21:48:01:0e:98 user@localhost The key's randomart image is: +--[ RSA 2048]----+ |+.o. | |ooE | |oo | |o.+.. | |.+.+.. S . | |....+ o + | | .o .... | | . .. . | | .... | +-----------------+
Next, execute this command in the terminal:
$ cat ~/.ssh/id_rsa.pub
The key will be displayed in the console. Copy it and paste it into the required field:
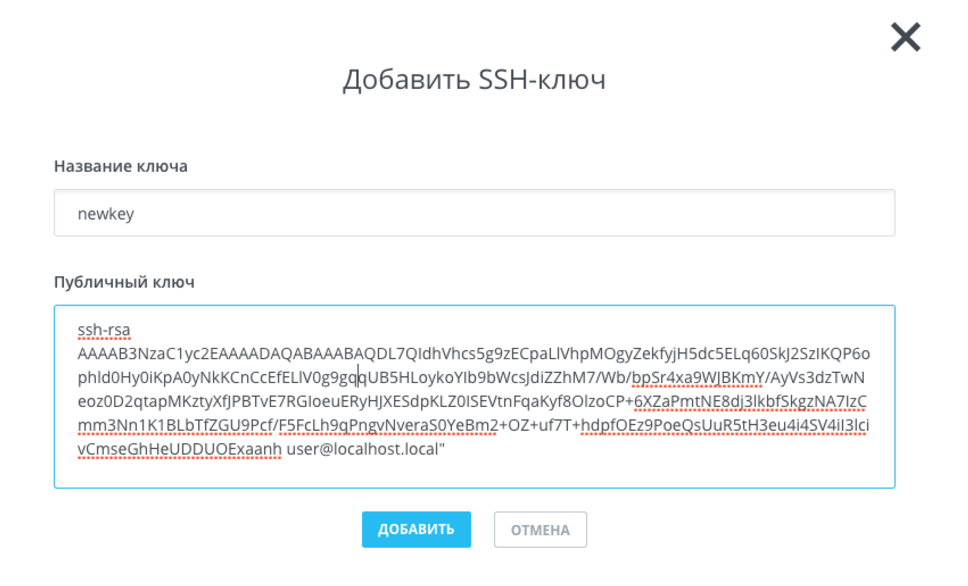
Click the Add button.
After adding the key, execute this command in the terminal:
$ ssh root@[Server IP address]
This will establish a connection to the server. You will not need to enter your password.
SSH Key for Windows
In Windows, you can use PuTTY client to connect to remote servers via SSH. You can download it here (link from the official website). PuTTY requires no installation – simply unzip the downloaded file to start using the program.
After unpacking, launch puttygen.exe.
Select the SSH-2 RSA key type with a 2048-bit length, then click “Generate”.
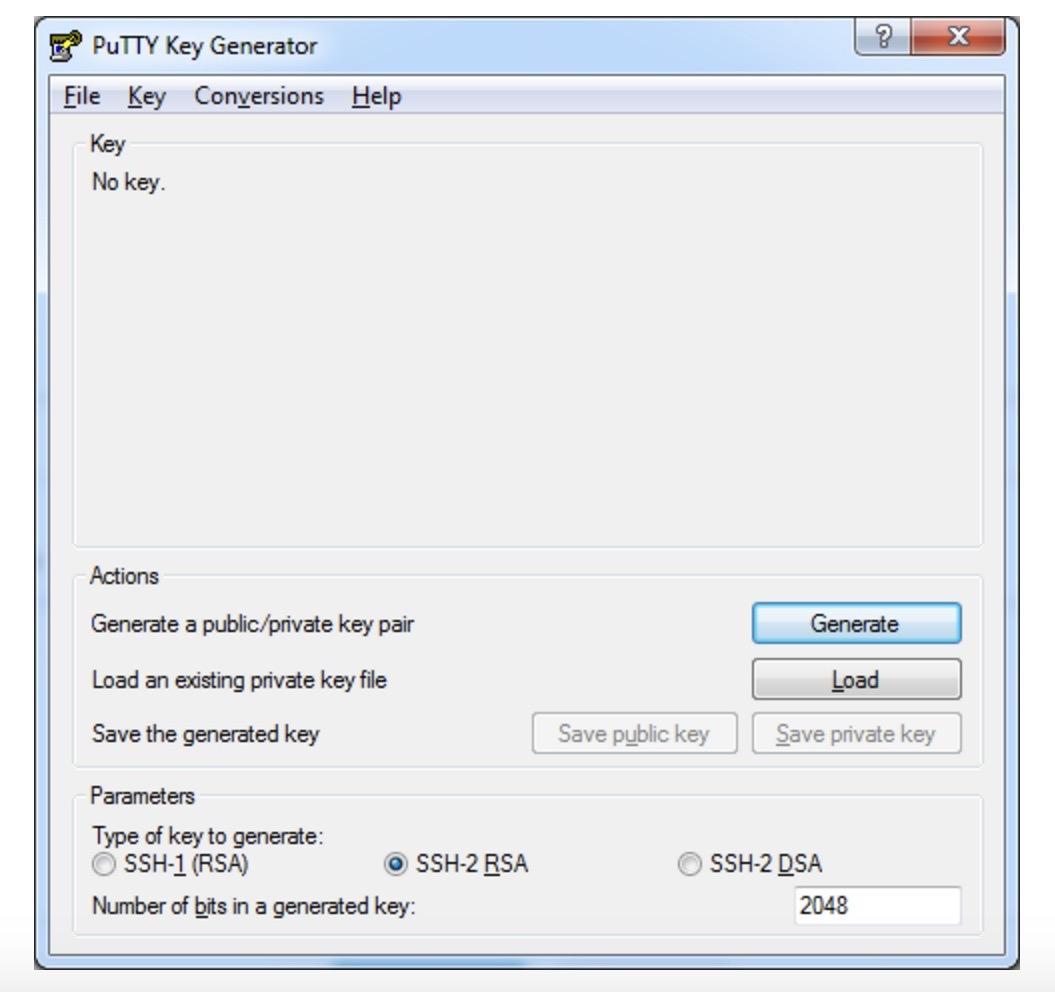
While the key is generating, move your cursor in an empty area of the window to generate pseudo-randomness.
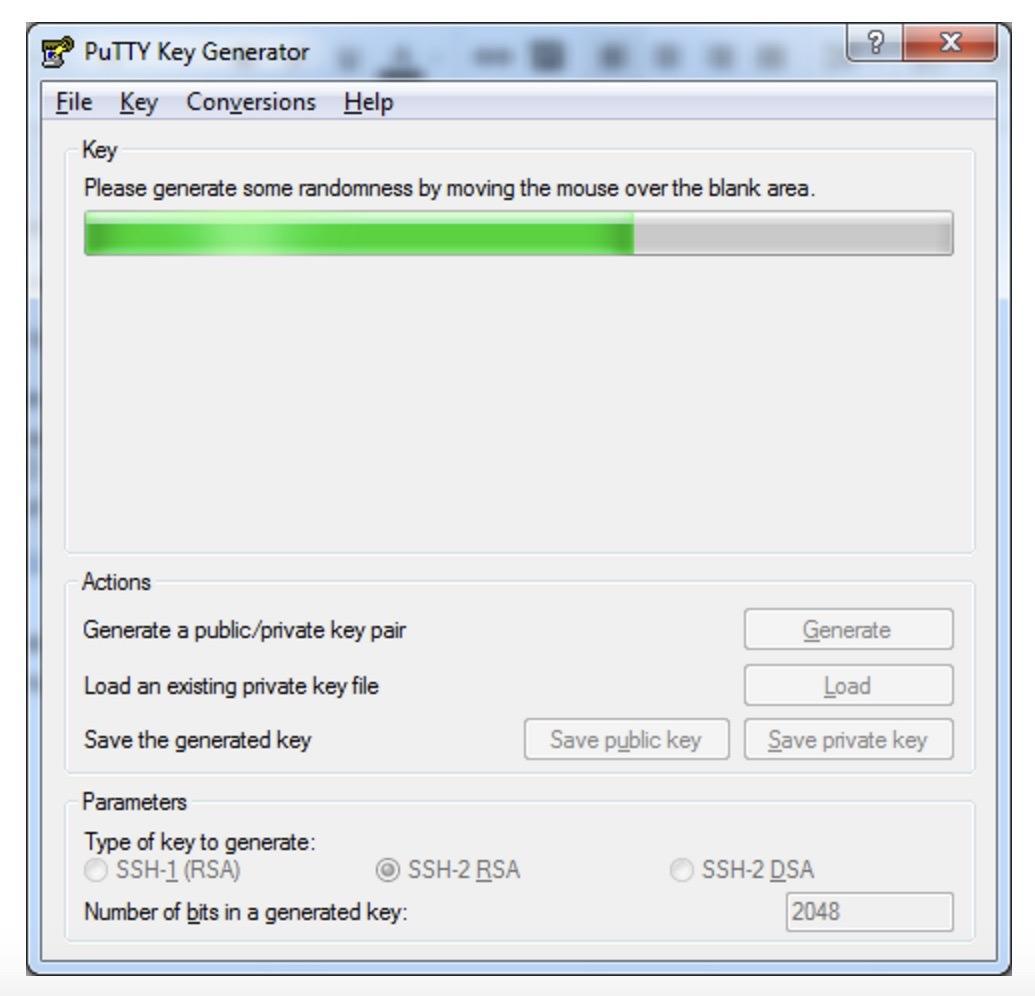
Save the generated key pair on your local machine using the “Save public key” and “Save private key” buttons.
Copy the generated key and paste it into the required field.
Conclusion
This guide demonstrates how to set up a secure connection to the server via an encrypted protocol by generating SSH keys on both Linux/MacOS and Windows. Now you can log into the system without needing to enter your account password.
