
Here’s how to set up virtual hosts, secure server access via HTTPS protocol, and configure security settings.
Introduction
Apache is a cross-platform HTTP server developed to address the shortcomings of the older NCSA HTTPd web server. The current stable version of Apache is 2.4.48. Apache features a modular system with high cross-platform capabilities, allowing to optimize the software for specific development needs.
This article discusses installing the Apache HTTP server on Ubuntu. This article uses the Ubuntu 20.04 Server release and Apache Server version 2. The system is deployed on Servercore’s “Cloud Platform” solution. Our test server will use a modest configuration of 1 CPU and 1 GB of RAM. This is more than enough to run a simple, low-load web application.
Setting up a Virtual Server
In this guide, we will use Servercore’s virtual environment.
Go to control panelIn the “Cloud Platform” section under the “Servers” tab, let’s create a new server.
We’ll use the minimum configuration.
In the settings, select the OS image for installation.
Let’s save the root password and create the server. After that, we’ll see the server’s IP address appear in the admin panel.
Now, we can connect to it via SSH.
The simplest way to connect is by using the PuTTY. This utility is cross-platform compatible. You can download it from the official website https://putty.org/.
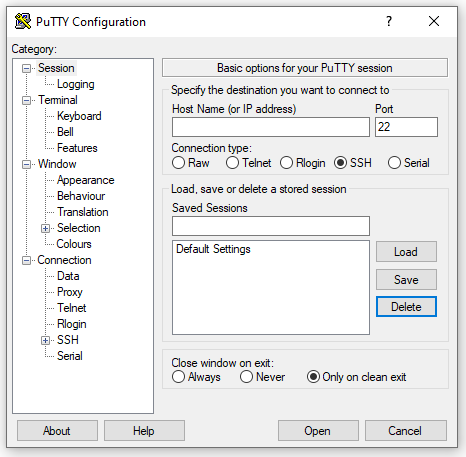
To connect, enter the previously obtained IP address in the “Host Name” (or “IP Address”) field, leaving other options unchanged.
After clicking “Open”, the terminal emulator will establish a connection to the server. You will need to enter your login+password combo. For now, let’s use the root login and password that we obtained during server creation.
login as: vlan48 vlan48@xx.xx.xx.18's password: Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 31 updates login as: vlan48 vlan48@xx.xx.xx.18's password: Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 31 updates can be applied immediately. To see these additional updates run: apt list --upgradable *** System restart required *** Last login: Tue Aug 3 09:51:36 2021 from xx.xx.xx.230 vlan48@apachi:~$
Installing Apache
To install and configure Apache, we will use a non-root user with administrative privileges. Privilege escalation through “sudo” will be used for most operations. Initially, you will need to download the information about the current package lists and dependencies.
sudo apt update
Following this operation, we will proceed with the installation of the Apache2 package, which is located in the standard repository; no additional need to be added.
sudo apt install apache2
Upon completion, the daemon will automatically start and be added to the autostart list.
Configure the Firewall for Apache
In Ubuntu, the default is to using ufw. Uncomplicated Firewall is a tool for configuring firewalls. If setting up on a virtual server, we suggest verifying that the utility is installed.
sudo: ufw: command not found
Needs to be installed:
sudo apt install ufw
Then we should re-request its status again:
Status: inactive
This means it is deactivated. Activating:
sudo ufw enable
Allowing HTTP on the server:
sudo ufw allow http
It’s important to allow SSH access at this moment. SSH is running on the standard port of the test server.
sudo ufw allow 22/tcp
Make sure to restart the process:
sudo ufw reload
Checking the Basic Apache Configuration
Currently, the server should be accessible from the Internet via HTTP. You can check this by entering the IP address in your browser’s search bar. We have already obtained the IP address from the server control panel.
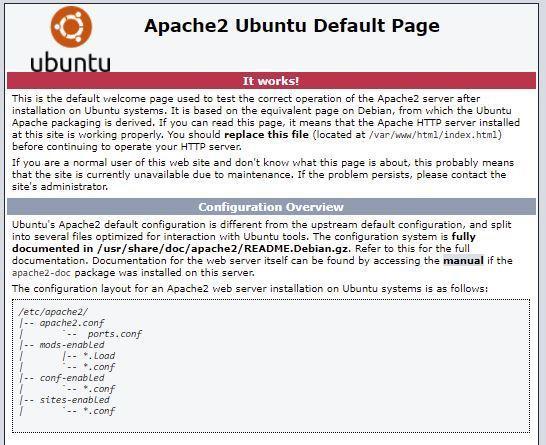
If you see the welcome message, it means that you have successfully completed the initial setup of the Apache server.
How to Launch Apache and Other Useful Commands
This section will detail basic commands for managing an Apache server. Although the daemon starts automatically, sometimes you may need to shut it down or reload the configuration.
How to check the status of the Apache daemon:
sudo systemctl status apache2
The output will show the current status. Two values are permitted.
Active:
apache2.service - The Apache HTTP Server
Loaded: loaded (/lib/systemd/system/apache2.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2021-07-15 09:49:55 UTC; 2 weeks 5 days ago
Docs: https://httpd.apache.org/docs/2.4/
Process: 535575 ExecReload=/usr/sbin/apachectl graceful (code=exited, status=0/SUCCESS)
Main PID: 718 (apache2)
Tasks: 55 (limit: 1105)
Memory: 12.9M
CGroup: /system.slice/apache2.service
├─ 718 /usr/sbin/apache2 -k start
├─535580 /usr/sbin/apache2 -k start
└─535581 /usr/sbin/apache2 -k start
Inactive:
apache2.service - The Apache HTTP Server
Loaded: loaded (/lib/systemd/system/apache2.service; enabled; vendor preset: enabled)
Active: inactive (dead) since Tue 2021-08-03 10:01:39 UTC; 2s ago
Docs: https://httpd.apache.org/docs/2.4/
Process: 535575 ExecReload=/usr/sbin/apachectl graceful (code=exited, status=0/SUCCESS)
Process: 544224 ExecStop=/usr/sbin/apachectl stop (code=exited, status=0/SUCCESS)
Main PID: 718 (code=exited, status=0/SUCCESS)
Sometimes an error may occur.
apache2.service - The Apache HTTP Server
Loaded: loaded (/lib/systemd/system/apache2.service; enabled; vendor preset: enabled)
Active: failed (Result: exit-code) since Tue 2021-08-03 10:07:39 UTC; 5s ago
Docs: https://httpd.apache.org/docs/2.4/
Process: 544394 ExecStart=/usr/sbin/apachectl start (code=exited, status=1/FAILURE)
Aug 03 10:07:39 apachi systemd[1]: Starting The Apache HTTP Server...
Aug 03 10:07:39 apachi apachectl[544401]: AH00526: Syntax error on line 134 of /etc/apache2/apache2.conf:
To back to the console from this status page, press Ctrl+C.
Deactivating:
sudo systemctl stop apache2
Activating:
sudo systemctl start apache2
Restarting:
sudo systemctl restart apache2
If the Apache configuration has been changed, it can be reloaded without breaking the current session from the hosts:
sudo systemctl reload apache2
Disabling web server launching at system startup:
sudo systemctl disable apache2
Enable launching at system startup:
sudo systemctl enable apache2
Configuring Apache Virtual Hosts
You can use Apache server to support a single web application. However, it’s often necessary to create and maintain multiple web resources on a single server.
Apache uses virtual hosts module for this purpose. It enables multiple web applications to be deployed on a single server with one IP address but different domain names. There are several pretty insightful articles and books on domain name theory, such as “DNS and BIND” by Cricket Liu and Paul Albitz. Management of domains and resource records was discussed in Servercore’s knowledge base.
Let’s proceed with setting up a virtual host.
In Ubuntu, virtual host configurations are stored in the /etc/apache2/sites-available. We need to access the default directory of virtual hosts. Obtaining the root directory from the default configuration file:
grep "DocumentRoot" /etc/apache2/sites-available/000-default.conf
Output:
DocumentRoot /var/www/html
Creating the new required directories without altering the root directory.
sudo mkdir -p /var/www/sample.net/html
By default, Apache searches for index.htm or index.html documents.
Let’s create a simple HTML5 document:
sudo touch /var/www/sample.net/html/index.html
Add some structure to the document by opening it in a text editor:
sudo nano /var/www/sample.net/html/index.html
Insert it into the file.
<!DOCTYPE html>
<html>
<head>
<title>Hello</title>
<meta charset="utf-8">
</head>
<body>
<h1>Hello Servercore!</h1>
</body>
</html>
To keep the default virtual host configuration, copy it into the settings directory that was just created for the new virtual host.
sudo cp /etc/apache2/sites-available/000-default.conf /etc/apache2/sites-available/sample.net.conf
Now, let’s open the copied file, review the main directives, and make the necessary changes. At this stage, we are only interested in the line that sets the path to the virtual host directory. Let’s change it to the path of the directory specifically created for it. This allows Apache to redirect requests specifically to our newly created virtual host when accessed.
sudo nano /etc/apache2/sites-available/sample.net.conf
Default virtual host file:
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
<VirtualHost *:80> – here we input the server’s IP address and the port used for this virtual host. Currently, we are using HTTP and a single IP address. Therefore, we use port number 80 and specify no address. Details on HTTPS configuration will be provided below.
ServerAdmin webmaster@localhost – this line establishes the link to the administrator; an active email address of the server maintenance specialist must be provided. Optional. Let’s add an address for the helpful support: support@servercore.com,.
DocumentRoot /var/www/html – this is the root directory of the virtual host. Must be used and correctly configured. In our case, it refers to the path to the directory previously created containing the index.html document. Making changes:
/var/www/sample.net/html
ErrorLog ${APACHE_LOG_DIR}/error.log – this is the path to the server’s log file. No changes are necessary. This is where daemon startup errors and non-client related errors will be stored.
CustomLog ${APACHE_LOG_DIR}/access.log combined – this directive is used for storing client access logs.
This concludes the file editing process. This is the minimal configuration needed to run a virtual host on an Apache web server. There is no need to alter the configuration further at this stage.
Save and exit the editor. Use Ctrl+O to save and Ctrl+X to exit.
Ready-made configuration file:
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin support@servercore.com
DocumentRoot /var/www/sample.net/html
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
To connect virtual hosts and modules in the Apache HTTP server, a set of commands is used:
a2enmod {module} – enables a module;
a2dismod {module} – disables a module;
a2ensite {virtual host config} – activates a virtual host;
a2dissite {virtual host config} – deactivates a virtual host.
We will need a2ensite to activate the host we created:
sudo a2ensite sample.net.conf
And a2dissite to deactivate the default one:
sudo a2dissite 000-default.conf
After making changes, we will need to reload the server configuration:
sudo systemctl reload apache2
Now we can access the newly created virtual host by its domain name.
In this guide, we do not use DNS; therefore, we will use the hosts file for name resolution.
In Windows, this file is located at C:\Windows\System32\drivers\etc\hosts.
And in Linux/Mac, it’s located at /etc/hosts.
Add the following line: 94.0.0.0 sample.net.
Where “94.0.0.0” is the previously obtained IP address of the server, and “sample.net” is the domain name of the virtual host.
Now, let’s open a browser and type “:sample.net” in the address bar.
This will display the web application we created earlier.
SSL for Apache
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are cryptographic protocols designed to secure data transmission between network nodes.
These protocols employ asymmetric encryption for authentication, symmetric encryption for confidentiality, and message authenticity codes. There’s no need to go into detail about the theory right now. Initially, it’s sufficient to know that these protocols ensure data confidentiality during client-server exchanges. Keys can be self-signed, meaning they are created and signed by the web server itself.
Such keys are suitable for HTTPS and encrypting data but are not trusted on the internet. Certificates can also be issued by certification authorities. These certificates not only encrypt data but are also automatically trusted by web browsers by default. While these certificates are typically paid, you can also use “Let’s Encrypt” for free. Using the service, you can create and certify a key.
In this case, the certificate will be valid on the internet but free of charge. This guide will set up basic encryption using a self-signed key generated on an Apache server.
Creating an SSL Certificate on the Server
To create and sign a certificate, you will need the OpenSSL package. It is pre-installed on the system. The certificate will now be created and signed, and the private and public keys will be moved to the necessary directories.
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/server-sample.key -out /etc/ssl/certs/server-sample.crt
Possible commands:
req -x509 – specify the certificate standard (x509 public key standard).
-nodes – disable password protection of the certificate. If you clear this option, you will be prompted for a password for the key, which must be entered each time the web server is started (preferably used in the production environment).
-days 365 – certificate validity period. Typically, a longer duration is set, but this is sufficient for a test server. Also note that the time and date must be correct on the web server.
-newkey rsa:2048 – commands to create a new certificate and the key at the same time. rsa:2048 denotes the key size.
-keyout /etc/ssl/private/server-sample.key – specifies the directory where the private key should be placed.
-out /etc/ssl/certs/server-sample.crt- – the certificate location directory.
server-sample.key and server-sample.crt – key and certificate names.
After entering the command, you’ll need to respond to some questions. Let’s review the list of directives:
Country Name (2 letter code) [AU]:RU – specifies the country
State or Province Name (full name) [Some-State]:LIP – specifies the region
Locality Name (eg, city) []:Lipetsk – specifies the city
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Sel – specifies the organization
Organizational Unit Name (eg, section) []:Sel – specifies the organization department
Common Name (e.g. server FQDN or YOUR name) []:94.255.255.255 – enter the domain name or server’s public IP address
Once the operation is complete, connect the SSL module to the Apache HTTP server. Earlier, we discussed the commands needed to do so. Here’s what you need:
sudo a2enmod ssl
After activating the module, you must restart the Apache daemon.
Now, let’s proceed to set up HTTPS for the virtual host. Modify its configuration file accordingly.
sudo nano /etc/apache2/sites-available/sample.net.conf
Firstly, change the <VirtualHost *:80> directive.
The port will be changed to 443 (the default port for HTTPS).
Insert “SSLEngine on” after the “DocumentRoot” line to activate SSL support on the web server.
Following that, add two lines indicating the paths to the key and certificate:
SSLCertificateFile /etc/ssl/certs/server-sample.crt SSLCertificateKeyFile /etc/ssl/private/server-sample.key
The virtual host configuration file now should look like this:
<VirtualHost *:443>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.sample.net
ServerAdmin support@servercore.com
DocumentRoot /var/www/sample.net/html
SSLEngine on
SSLCertificateFile /etc/ssl/certs/server-sample.crt
SSLCertificateKeyFile /etc/ssl/private/server-sample.key
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Before the web check, add a security rule that allows access:
sudo ufw allow https
Additionally, reload the Apache web server configuration:
sudo systemctl reload apache2
Now, when accessing the server via HTTPS:sample.net , the browser will alert you that the certificate is not secure. By ignoring this alert, you will see the web application created earlier.
This concludes the SSL setup.
Apache Web Server Configuration Files and Directories
The listed files and directories are used in configuring the Apache server. This document does not contain any unique settings. This section is intended for informational purposes only.
/etc/apache2 – directory for Apache configuration files.
/etc/apache2/apache2.conf – the primary configuration file for the server. It manages several server settings. For instance, here’s where you would need to enable reading .htaccess file.
/etc/apache2/envvars – file containing environment variable values for Apache.
/etc/apache2/magic – instructions for identifying file types on both server and client.
/etc/apache2/ports.conf – sets up default listening ports.
/etc/apache2/sites-available/ – directory for virtual hosts configurations.
/etc/apache2/sites-enabled/ – contains information on active virtual hosts.
/etc/apache2/conf-available/ – directory for non-virtual host settings.
/etc/apache2/conf-enabled/ – contains links to enabled non-virtual hosts.
/etc/apache2/mods-available/ and /etc/apache2/mods-enabled/ – directories for modules. Modules and their settings can be found here.
/var/www – directory used to store web applications. Virtual hosts are also typically stored here. Can be modified as necessary.
/var/log/apache2 – log files directory, contains two files previously mentioned in this guide.
Apache Web Server Security
A server facing the internet is inherently at risk, regardless of its assigned tasks. It may be targeted by malicious actors who could disrupt its functioning. Let’s find out how to protect against unauthorized SSH access by untrusted users.
In Linux systems, Fail2ban is an excellent choice for this purpose. Its functions by monitoring server access logs. Based on the specified number of attempts, it determines whether to block the IP address suspected of initiating an intrusion.
Installing and Configuring Fail2ban
sudo apt-get install fail2ban -y
The utility comes with built-in protection against password brute force attacks. However, in our case, several modifications must be made before activation.
/etc/fail2ban/jail.conf – manages the security settings for specific services.
It is not advisable to modify it, so we will create a new file with the .local extension. These files have a higher priority than the .conf file for Fail2ban.
sudo nano /etc/fail2ban/jail.local
Let’s configure settings to protect SSH:
[sshd] enabled = true port = 22 filter = sshd logpath = /var/log/auth.log maxretry = 4 bantime = 60
Line by line:
The [sshd] directive safeguards SSH access upon authorization failure;
enabled = true – status;
port = 22 – port number;
filter = sshd – the name used to search the service logs;
logpath = /var/log/auth.log – the log file where filter search results are retrieved from;
maxretry = 4 – number of failed attempts;
bantime = 60 – duration of blocking in seconds. This section is here for testing purposes; in production, the blocking duration is usually for longer.
Configuration complete, let’s add and start the Fail2ban daemon, then check its functionality.
sudo systemctl enable fail2ban sudo systemctl start fail2ban
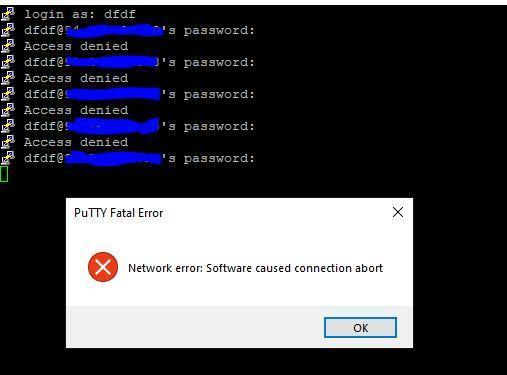
As observed, access is blocked after exceeding the number of allowed authorization attempts.
Access will be restored after 60 seconds.
To unlock access, the following command is used:
sudo fail2ban-client set sshd unbanip ip_add
ip_add — заблокированный адрес.
Conclusion
This concludes the setup instructions for the Apache web server. In summary, we’ve configured one of the most popular web servers and secured access via HTTPS, explored virtual host configuration, and protected the server from malicious attacks. At this stage, the administrator can independently manage and configure the Apache web server on Linux.
