
When browsing on public Wi-Fi, working remotely, or simply trying to access geo-restricted content, your data is vulnerable to prying eyes and constantly at risk. Hackers, government surveillance, and even internet service providers (ISPs) can track your online activity, collect personal information, and compromise your security.
This is where a Virtual Private Network (VPN) comes in handy.
According to Statista, 23.1% of internet users worldwide utilize VPNs. Surfshark estimated that over 1.6 billion people use VPNs. Not only are VPNs popular among individual users, but a significant majority of organizations—93%—currently implement VPNs to protect sensitive data and ensure secure remote access for employees.
But what exactly is a VPN and how does it work to protect your online data and activities?
This comprehensive guide will take you through everything you need to know about VPNs—from their history and different types to the technical details about encryption protocols, step-by-step setup options and best practices. Whether you’re a beginner or looking for in-depth understanding, this guide helps you understand why VPN technology has become a must-have for individuals and businesses.
VPN Meaning
VPN is a secure network tunnel or connection that encrypts your Internet traffic. That way, it disguises your online identity, ensuring privacy and anonymity. By routing traffic through VPN servers located in different parts of the world, the VPN service masks or hides the user’s IP address and encrypts all data transmitted over the Internet in real-time, preventing ISP from tracking and/or intercepting your activities.
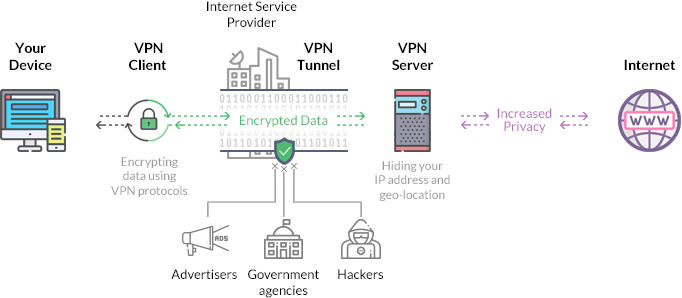
This infographic above illustrates how a VPN enhances online privacy and security.
- Your Device–A computer or mobile device connects to the internet through a VPN.
- VPN Client–The VPN software encrypts outgoing data using secure VPN protocols.
- VPN Tunnel–The encrypted data travels through a secure tunnel, preventing advertisers, government agencies, and hackers from intercepting or monitoring sensitive information.
- VPN Server–The VPN server operated by a VPN service provider decrypts the data, masks the user’s IP address, and assigns them a new IP address which appears as though they’re browsing from a different location, ensuring anonymity.
- Internet–The user accesses websites and online services with increased privacy and confidentiality as their real identity and location remain hidden.
Benefits of a VPN connection
A VPN ensures your information remains private and protected from malicious actors, such as hackers, cybercriminals, or even governments. Beyond security, a VPN enhances anonymity by masking your IP address and location. This prevents websites, advertisers, and ISPs from tracking your browsing activities.
Without a VPN, ISPs can collect and sell your data to third parties, exposing you to targeted ads and potential privacy breaches. You regain control over your online presence and browsing habits by using a VPN.
For remote workers, a VPN is an invaluable tool for accessing company resources securely. Many businesses require employees to connect through a VPN to ensure encrypted communications and internal data protection. Whether you’re working from home or traveling, a VPN allows seamless and safe access to corporate networks without compromising security.
History of VPNs
Prior to VPNs, businesses and organizations depended on leased lines and dial-up connections for private communication. These methods were expensive and unscalable for widespread internet use. One of the earliest concepts resembling a VPN was packet switching, which allowed data to be sent in small, manageable units over a shared network. However, this technique still left data vulnerable to tracking and interception by third parties.
The first true VPN technology was developed by Microsoft in 1996 when a team of engineers created the PPTP (Point-to-Point Tunneling Protocol) protocol. The technology allowed users to establish encrypted connections over public networks. It was an early method for ensuring secure connections over the Internet, laying the groundwork for modern VPNs.
By the early 2000s, VPNs were mainly used by enterprises for secure remote access to internal systems. However, the rise of cyber threats and data breaches spurred interest in VPN technology beyond corporate use.
Different Types of VPN
Different VPN types serve distinct purposes, whether for businesses securing internal networks or individuals protecting personal data. Let’s explore the key types of VPNs and their functionalities.
- SSL (Secure Sockets Layer) VPNs use HTTPS web protocols to establish secure connections between the user’s device and the VPN gateway. SSL works through a web browser, does not require the installation of additional programs, and is popular due to its ease of use. Such VPNs create secure remote access to internal networks, so they are chosen by companies where employees need to connect to the organization’s resources from external locations.
- Client-to-server or remote access VPN allows users to securely connect to a private network, encrypting all transmitted data to protect against cyber threats. It enables remote employees to access company resources safely, ensuring privacy even on unsecured networks. While it enhances security, it requires VPN client software and may introduce latency depending on server location.
- Site-to-Site VPNs are used to establish secure connections between two or more geographically dispersed networks. This VPN connects networks and reduces the need for individual VPN client installations. Companies with multiple offices or branch offices often use it to organize a geographically distributed private network.
- An intranet VPN secures internal communications within an organization, allowing employees to access company resources securely from any location. It provides encrypted remote access to employees and works similarly to a site-to-site VPN but is restricted to a company’s internal network.
- An extranet VPN extends secure network access to external partners, suppliers, or clients without exposing the entire internal network. Businesses use this setup to collaborate securely with third parties. It requires careful access management to prevent data leaks and holds security risks if external partners don’t follow best practices.
- A mobile VPN is designed for users who frequently switch networks or move between different locations, such as field workers or remote employees. Unlike traditional, mobile VPNs maintain a secure connection even if the user changes Wi-Fi networks or switches to mobile data. This is ideal for users on the move, ensuring continuous protection, but can consume more battery and bandwidth on mobile devices. Also, mobile may have slower connection speeds compared to traditional VPNs.
How Does a VPN Work?
A VPN creates a secure and encrypted connection between a user’s device and the Internet, masking their IP address and protecting data from interception. This means that, if you browse online with a VPN, a VPN server becomes your source, and third parties cannot see the data you send or receive or the sites you visit. Such is achieved through different VPN protocols, each offering varying levels of security, speed, and compatibility.
OpenVPN
A widely used open-source VPN protocol known for its strong security and flexibility. It employs SSL/TLS encryption to secure the connection between a client and a VPN server, ensuring safe data transmission. OpenVPN supports AES-256 encryption, which is considered military-grade security, and allows users to choose between UDP for faster performance or TCP for more reliable connections.
Its open-source nature enables continuous community-driven improvements, making it a highly customizable solution. However, setting up OpenVPN can be complex, and it tends to be slower than newer protocols like WireGuard.
SSTP
Developed by Microsoft, this is a VPN protocol that leverages SSL/TLS encryption over port 443, the same port used by HTTPS traffic. This makes it particularly effective at bypassing firewalls, as it blends seamlessly with regular Internet traffic. SSTP uses AES encryption to secure data, ensuring strong protection against cyber threats.
Its biggest advantage is its native integration into Windows, making deployment simple for users within Microsoft environments. However, it is a closed-source protocol controlled by Microsoft, which limits transparency and restricts support for non-Windows devices.
IKEv2/IPSec
A stable VPN protocol designed for users who frequently switch networks, such as mobile users transitioning between Wi-Fi and mobile data. It employs the Diffie-Hellman key exchange for authentication and implements AES-256 encryption for secure data transmission.
One of its key strengths is its ability to automatically re-establish connections after interruptions, making it a preferred choice for mobile users. It is natively supported on major operating systems, including Windows, macOS, iOS, and Android. However, it is not as widely supported as OpenVPN and can sometimes be blocked by firewalls.
L2TP/IPSec
This protocol combines the Layer 2 Tunneling Protocol with IPSec encryption to enhance security. While L2TP does not provide encryption, IPSec adds AES-256 encryption to ensure secure data transmission. It is often used when OpenVPN is unavailable, but its reliance on UDP port 1701 makes it susceptible to firewall restrictions.
Additionally, L2TP/IPSec employs double encapsulation, which improves security but negatively impacts connection speed. Despite these drawbacks, it remains a widely supported protocol and is often included in built-in VPN clients across various operating systems.
PPTP
PPTP (Point-to-Point Tunneling Protocol) is one of the oldest VPN protocols, initially developed by Microsoft in the 1990s. It’s known for its fast connection speeds but is widely regarded as insecure by modern standards. PPTP relies on 128-bit encryption, which is considered weak and vulnerable to attacks.
While it is easy to set up and compatible with nearly all devices, its security flaws make it unsuitable for protecting sensitive data. Given its outdated encryption methods, most modern VPN services discourage its use for anything beyond basic, low-risk applications.
WireGuard
A modern VPN protocol designed to offer superior speed, security, and efficiency compared to traditional protocols. It utilizes the ChaCha20 encryption algorithm, which provides high-performance encryption while being faster than AES-256. With a minimal codebase of under 4,000 lines, WireGuard is lightweight, reducing potential security vulnerabilities.
Operating over UDP, it delivers faster performance than TCP-based protocols and is integrated into the Linux kernel for seamless operation. However, as a relatively new protocol, it is not yet widely supported like OpenVPN. It also lacks built-in obfuscation features for bypassing restrictive networks.
Must-Have Features of a Good VPN
A high-quality VPN goes beyond basic encryption, ensuring security, privacy, and seamless browsing. Below are features for an ideal VPN:
Strong Protocols for Reliable Encryption: VPNs must use strong encryption protocols like OpenVPN, WireGuard, and IKEv2/IPSec to protect data while maintaining speed. Outdated protocols like PPTP are vulnerable and should be avoided.
IP Address Protection to Maintain Anonymity: VPNs hide the user’s actual IP address to prevent tracking and ensure privacy. Leak protection is essential, even if the connection drops unexpectedly.
A Range of Servers Across Many Locations: VPNs improve performance and access by offering servers in multiple countries. More servers reduce congestion, enhance speed, and help bypass geographic restrictions.
A Zero-Log Policy for True Privacy: VPNs should follow a strict no-logs policy to prevent storing browsing or connection data. Privacy remains intact, protecting users from legal demands, security breaches, or third-party exposure.
A Kill Switch for Uninterrupted Protection: VPNs need a kill switch to prevent accidental data leaks when the connection drops. Internet access is immediately blocked until a secure VPN connection is restored.
Mobile Compatibility for Secure Browsing Anywhere: VPNs must support mobile devices with dedicated apps for iOS and Android. Secure browsing remains available on cellular networks and public hotspots.
Flexible Authentication for Extra Security: VPNs enhance security with multi-factor authentication (MFA), requiring additional verification beyond a password. Biometric scans, one-time codes, or hardware tokens help prevent unauthorized access.
Reliable Customer Support When It’s Needed: VPNs should offer responsive customer support to resolve technical issues quickly. Live chat, email, and knowledge bases help users troubleshoot effectively.
Premium Pricing for a Better Experience: VPNs with paid plans provide stronger encryption, faster speeds, and premium features. Free options come with security risks, slower performance, and intrusive ads.
Setting up a VPN
Whether you’re looking for personal online security, company-wide network protection, or a dedicated server-based VPN, this guide covers different ways to set up a VPN.
Using a VPN Client
A VPN client is an application provided by a VPN service provider that automatically configures and connects to a VPN server.
Steps to set up a VPN client:
- Choose a VPN provider – Popular services include NordVPN, ExpressVPN, and ProtonVPN.
- Download & Install – Install the VPN client on your device (Windows, macOS, Linux, Android, iOS).
- Log In – Enter your account credentials.
- Choose a Server – Select a VPN server based on location (e.g., nearby for speed, or a specific country for bypassing geo-restrictions).
- Connect – Click the Connect button to establish a secure connection.
Best for: General users who want a quick and secure connection.
Using a VPN Browser Extension
Many VPN providers offer Chrome, Firefox, Edge, and other browser extensions—these work as proxy VPNs, encrypting only your browser traffic while leaving other apps unprotected.
Steps to set up a VPN browser extension:
- Install the Extension – Go to the Chrome Web Store or Firefox Add-ons page and install a VPN extension (e.g., Surfshark, NordVPN, Windscribe).
- Log In – Enter your VPN account credentials.
- Select a Server – Pick a country or location.
- Enable the VPN – Click the connect button to activate the VPN for your browser.
Best for: Users who need quick VPN access for browsing but don’t want system-wide VPN coverage.
Setting Up a VPN on a Router
Instead of setting up a VPN on every device, you can configure it directly on your router. This ensures that all connected devices (PCs, smartphones, smart TVs, gaming consoles) use the VPN without individual installations.
Steps to set up a VPN on a router:
- Check Router Compatibility – Not all routers support VPNs. Look for routers with OpenVPN support (e.g., ASUS, Netgear, Linksys, TP-Link).
- Download VPN Configuration Files – Your VPN provider should provide OpenVPN or WireGuard configuration files (.ovpn or .conf).
- Access Router Settings – Log into your router’s admin panel (usually at 192.168.1.1).
- Find the VPN Settings – Navigate to VPN Client or OpenVPN Setup (varies by router).
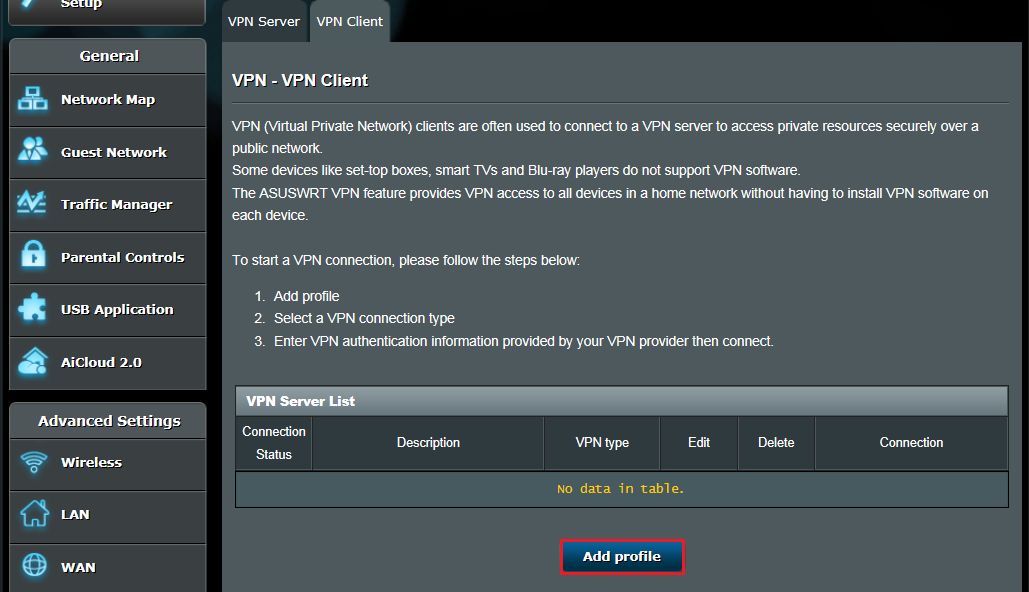
5. Upload Config File – Import the .ovpn/.conf file, enter credentials, and save settings.
6. Enable VPN – Activate the VPN to route all traffic through the encrypted tunnel.
Best for: Users who want VPN protection for all home or office network devices.
A VPN on Smartphone or Other Devices
Most modern VPN services support multiple devices, including:
- Smartphones (Android & iOS) – VPN apps available on the Google Play Store & Apple App Store.
- Smart TVs – Some smart TVs support VPN apps, while others require router-level VPN.
- Gaming Consoles (PS5, Xbox, Nintendo Switch) – No built-in VPN support, but can use a VPN-enabled router.
- Tablets & IoT Devices – VPNs can be used via router setups or mobile apps.
Setting Up a VPN with Servercore’s Infrastructure
A virtual server gives you full control over your infrastructure and settings while providing a high level of security. Servercore offers ready-made virtual machine images that allow you to quickly set up a VPN. Users receive a virtual server with pre-installed Windows OS images and a dedicated public IP address.
Steps to set up a VPN with Servercore:
- Deploy a cloud server from Servercore.
2. Install the VPN protocol – Use OpenVPN or WireGuard.
3. Configure the VPN – Create a server configuration (server.ovpn for OpenVPN or wg0.conf for WireGuard).
4. Set encryption keys and server parameters.
5. Define user access rights.
6. Load client files – Create .ovpn or .conf files for the devices to be connected.
7. Connect clients – Import configuration files into VPN clients on Windows, macOS, or mobile devices.
Best for: Advanced users or businesses wanting complete control over their VPN setup.
Also, check our complete guide for installing and configuring pfSense.
The Limits of VPN Protection
A VPN is one of the most effective tools for protecting online privacy. However, it doesn’t guarantee total anonymity or security in all situations. VPN providers can still see user activity unless they follow a strict no-logs policy. Websites continue to collect data through cookies, browser fingerprinting, and tracking scripts, while ISPs can detect VPN usage, even if they cannot see the actual browsing activity. Additionally, logging into personal accounts reveals your identity regardless of VPN protection.
To enhance anonymity:
- Choose a no-logs VPN.
- Browse in private mode.
- Combine a VPN with Tor.
- Disable tracking scripts in browser settings.
While a VPN secures data transmission, it doesn’t prevent hacking, such as phishing attacks, malware infections, zero-day exploits, or social engineering scams. Clicking on a malicious link, downloading an infected file, or falling for a scam remains a risk even with an active VPN connection.
To stay secure:
- Enable multi-factor authentication.
- Use strong and unique passwords.
- Use a password manager.
- Keep software updated.
VPNs do not function as antivirus software, though some providers include features that block known malicious websites. A VPN alone does not scan for or remove malware.
To prevent infections:
- Rely on dedicated antivirus programs.
- Avoid untrusted downloads.
- Be cautious with email attachments.
- Configure a firewall to block unauthorized connections.
Dangers of free VPNs
Free VPN services should generally be avoided due to potential data collection. Public VPN services may lack security and certification checks, and their privacy policies may include clauses that allow them to collect and share your data with third parties. Some free VPN services turn users’ devices into proxy servers that attackers use for cybercrime.
In May 2024, an international operation led by the U.S. Department of Justice dismantled the largest botnet in history, 911 S5. Cybercriminals had used it for large-scale attacks, financial fraud, threats, child exploitation, and evading export restrictions. The botnet infected Windows-based computers worldwide, integrating them into a network of 19 million unique IP addresses. Malware was spread through VPN programs like MaskVPN and DewVPN, turning infected devices into proxy nodes for criminal activities.
The botnet functioned as a commercial service, allowing criminals to mask their locations, steal data, bypass fraud detection, and distribute malicious content. The network enabled cybercriminals to appear as legitimate users by selling access to compromised IP addresses.
VPN Alternatives for Business
Many companies now adopt alternative solutions for better security, flexibility, and performance:
- Zero Trust Network Access (ZTNA) grants access based on identity and device security, reducing insider threats and unauthorized access.
- Software-Defined Perimeter (SDP) hides corporate resources from unauthorized users, ensuring secure access without exposed endpoints.
- Cloud Access Security Brokers (CASB) protect cloud applications by enforcing security policies, monitoring access, and preventing data leaks.
- Secure Web Gateways (SWG) block malicious content and enforce security policies while allowing direct and secure internet access.
- Secure Access Service Edge (SASE) integrates multiple security technologies into a cloud-based platform, eliminating VPN performance issues.
VPN Alternatives for Enterprises
Enterprises need scalable security solutions beyond traditional VPNs:
- Enterprise-Grade ZTNA verifies users before granting access to specific resources, minimizing security risks.
- SD_WAN optimizes traffic routing, reducing latency and improving performance.
- Identity and Access Management (IAM) ensures only verified users access critical systems through Single Sign-On (SSO) and multi-factor authentication (MFA).
- Cloud-Native Security Platforms provide real-time threat detection for SaaS and hybrid environments, offering more advanced security than VPNs.
- SASE unifies networking and security into a single cloud-based solution, enabling secure access without VPN limitations.
Conclusion
VPNs are a critical tool for enhancing online privacy and security, offering encryption and anonymity by masking IP addresses and securing data transmissions. Creating your own VPN server is a reliable way to protect your data and ensure privacy. Using WireGuard or Xray on a Servercore virtual server not only increases security, but also gives you full control over your connection.
Servercore plays a pivotal role in strengthening business security by providing tailored solutions for managing and securing data traffic. It helps businesses optimize their networks with enterprise-grade technologies, ensuring reliable access control, data protection, and streamlined security management.